4.9 KiB
4.9 KiB
Lab 1.1, Routing and DMZ
Configuring rw01
- changing the champuser password:
password123! - set hostname to
rw01-charlotte(reference) - add sudo user
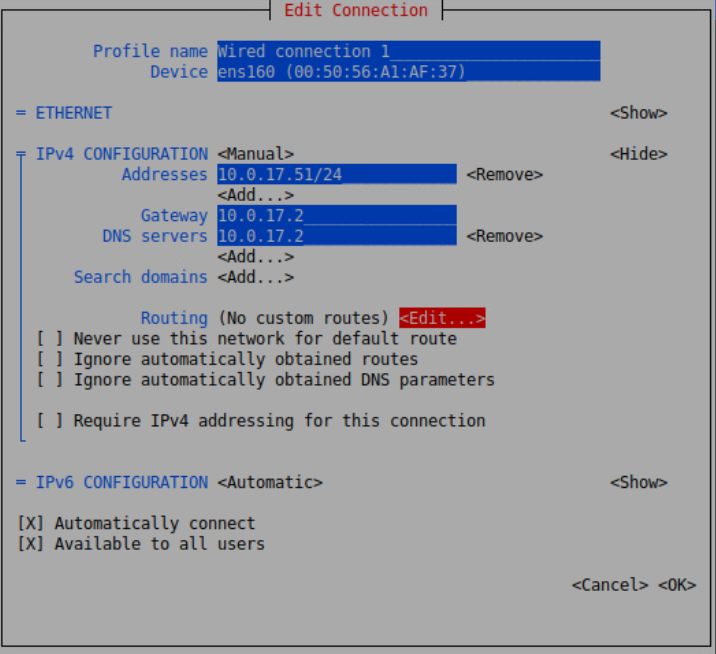
charlotte:password123!(reference) - Make sure you have a static ip that matches the one in the IP assignments spreadsheet: use nmtui, set IP to
10.0.17.51/24and gateway/DNS to10.0.17.2
fw01, gateway/router/firewall (VyOS doc)
default creds: vyoz:Ch@mpla1n!22
set hostname
configure
set system host-name fw01-charlotte
commit
save
Repeat exit until you get to a login prompt. Then you should see your new hostname, so go ahead and log in back to configure.
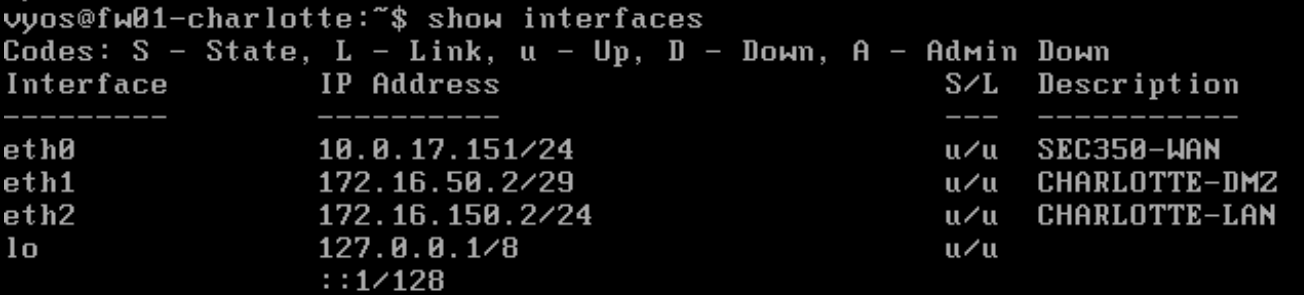
configure interfaces
configure
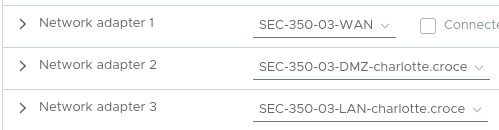
set interfaces ethernet eth0 description SEC350-WAN
set interfaces ethernet eth1 description CHARLOTTE-DMZ
set interfaces ethernet eth2 description CHARLOTTE-LAN
set interfaces ethernet eth0 address 10.0.17.151/24
set interfaces ethernet eth1 address 172.16.50.2/29
set interfaces ethernet eth2 address 172.16.150.2/24
commit
save
configure gateway & DNS
configure
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2
set system name-server 10.0.17.2
commit
save
Configuring NAT and DNS Forwarding for DMZ
configure
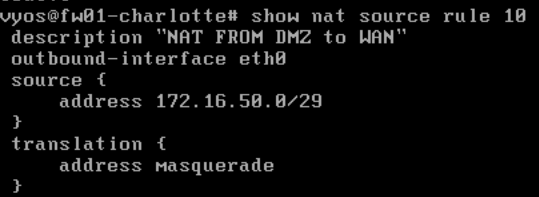
set nat source rule 10 description "NAT FROM DMZ to WAN"
set nat source rule 10 outbound-interface eth0
set nat source rule 10 source address 172.16.50.0/29
set nat source rule 10 translation address masquerade
set service dns forwarding listen-address 172.16.50.2
set service dns forwarding allow-from 172.16.50.0/29
set service dns forwarding system
commit
save
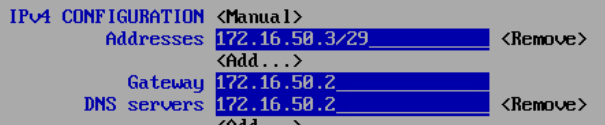
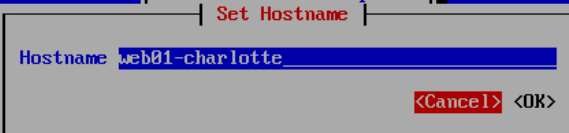
web01, web server
basics
configure httpd
- install httpd (reference)
on rw01, testing web service
- any address in your DMZ should route via fw01’s WAN interface. We do this with a static route on rw01
- anything addressed to the 172.16.50.0/29 network will go through the 10.0.17.151 router
sudo ip route add 172.16.50.0/29 via 10.0.17.151
sudo systemctl restart NetworkManager
traceroute 172.16.50.3
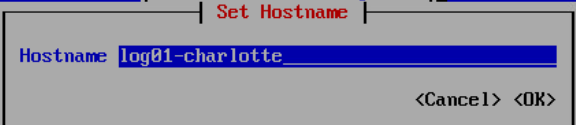
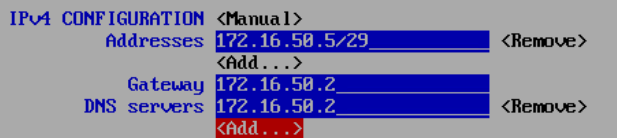
log01, rsyslog server
log01 will be initially in the DMZ, later we will change this to a segmented network area
basics
rsyslog setup
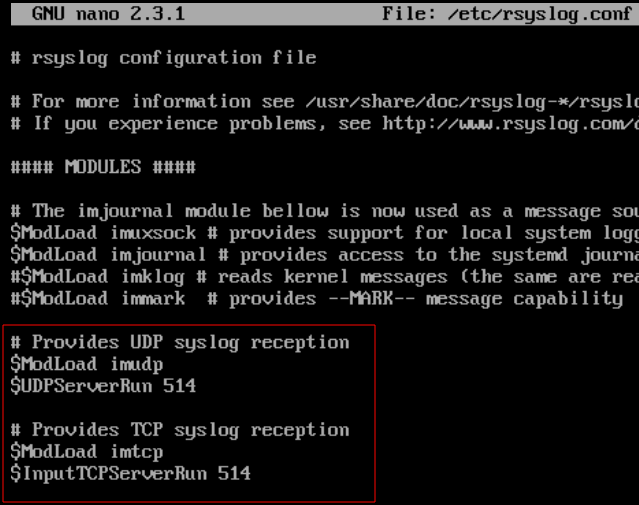
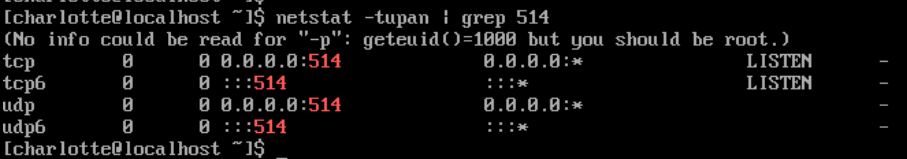
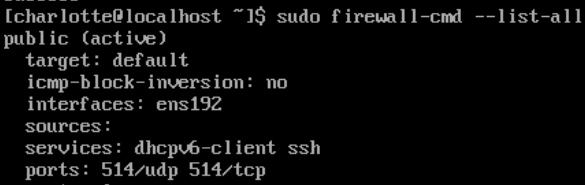
allow UDP and TCP 514 for syslog traffic
sudo firewall-cmd --add-port=514/tcp --permament
sudo firewall-cmd --add-port=514/udp --permament
sudo firewall-cmd --reload
On log01, the /etc/rsyslog.conf file needs to be modified to receive syslog messages over ports 514 tcp and udp. Uncomment the appropriate lines (see below) and restart the rsyslog service.